Our threat detection system creates a comprehensive security barrier at the application entry point. Using advanced browser fingerprinting technology, we generate unique visitor profiles and assess risk in real-time – ensuring only legitimate users can access your systems.
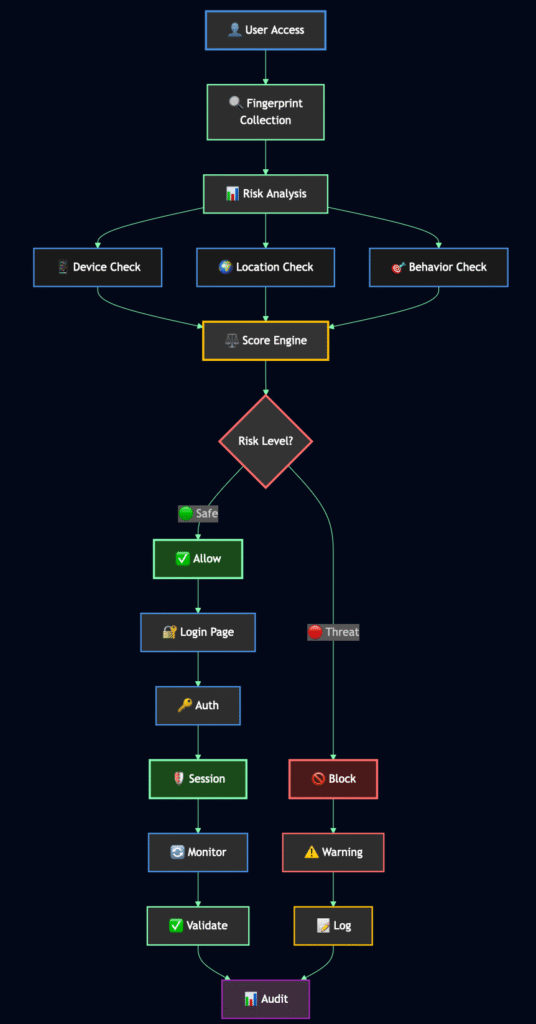
How It Works
Step 1: Fingerprint Analysis
Generate unique browser/device signatures using 40+ data points including screen resolution, browser metadata, and hardware characteristics.
Step 2: Risk Assessment
Evaluate threats using configurable scoring parameters customized for your organization’s security requirements.
Step 3: Threat Blocking
Block high-risk access attempts before the login page is even displayed to suspicious users.
Step 4: Session Monitoring
Continuous validation throughout the user session using visitor ID and security token verification.
Advanced Security Capabilities
Device Fingerprinting Intelligence
Our fingerprinting creates unique device signatures using:
- Screen resolution, color depth, and CPU concurrency
- Browser metadata and WebGL/GPU rendering analysis
- Local timezone and language settings
- Touch capabilities and font rendering patterns
- Audio fingerprint signals
Geolocation Cross-Validation
Automatically detects suspicious access patterns by:
- Comparing IP timezone with device local timezone
- Identifying VPN or Tor routing attempts
- Detecting emulated browser environments
- Flagging spoofed or manipulated client behavior
- Canvas fingerprint signals
Real-Time Blocking Engine
Threat Response Capabilities:
- Blocks access before login page loads
- Displays security warning to suspicious users
- Prevents backend exposure to threats
- Logs all events for audit compliance
Session Continuity Validation
- Generated visitor ID tied to security tokens
- Continuous validation throughout session
- API call authentication between login/logout
- Prevents session hijacking and takeover
Configurable Risk Parameters
Each client can customize threat detection sensitivity based on their specific security requirements. Our system evaluates multiple risk factors to create a comprehensive threat score that protects your data from the very first point of contact.
- Timezone Mismatch
- Software GPU Rendering
- Low Screen Resolution
- Touch Support On Desktop OS
- Missing Audio Fingerprint
- Fonts Missing OR Less Than 10
- Canvas Fingerprint Unavailable
- Incomplete Canvas
- Canvas Too Short
- All Canvas Values Identical
- Catch Block
- Total Block Score
Intelligent Scoring System
Our configurable risk engine allows organizations to set custom thresholds for each parameter. When the total risk score exceeds your defined threshold, the system automatically blocks access and logs the event for security analysis – protecting your data from the very first point of contact.
Industry Applications
Financial Services
Block bot attacks and anonymized fraud attempts during banking portal access. Protect against credential stuffing and account takeover attempts.
E-Commerce Platforms
Reduce account takeover risks and protect customer data from automated attacks and malicious bot activity.
Healthcare Systems
Ensure HIPAA-compliant access from registered devices only, protecting your sensitive patient data from unauthorized access attempts.
Government & Defense
Enforce CMMC Level 2 and FedRAMP High compliance with stricter scrutiny for remote access attempts to classified systems.
Compliance & Integration
Regulatory Alignment
- Zero Trust Architecture (ZTA) – Never trust, always verify principle
- CMMC Level 2 & Level 3 – Advanced cybersecurity practices
- FedRAMP High – Government-grade security controls
- HIPAA Compliance – Healthcare data protection requirements
- SOC 2 Type II – Comprehensive audit and compliance logging
Platform Integration
Seamlessly integrates across all Enablement® platform interfaces including –
Single Page Application
Java Spring Security
RDBMS, Cache
Native mobile apps iOS/Android
JWT API gateway protection
Technical Configuration
Deployment Options
- Cloud-native deployment
- On-premises installation
- Hybrid cloud configuration
- Multi-tenant isolation
Configuration Parameters
- Enable/disable blocking
- Centralized logging endpoint
- Custom risk scoring
- Continuous monitoring
Protect Your Organization Today
Stop threats before they reach your login page. Implement advanced fingerprint-based threat detection with customizable risk parameters tailored to your security requirements.
